by David Ponder | Mar 18, 2019 | Chief Compliance Officers, GRC Implementation, Risk Management
The Most Overlooked Element of Successful GRC Most GRC / IRM material focuses on things that are unique to the world of business and technology risk. This often makes sense since there is so much to consider when working with GRC. Thousands of GRC guides,...
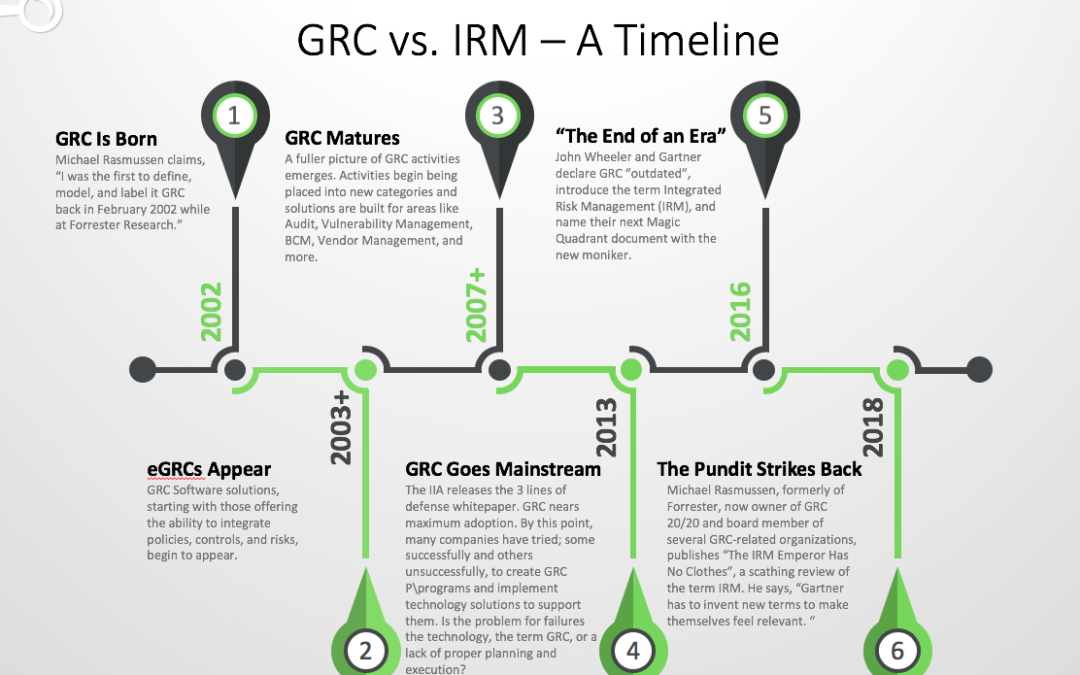
by David Ponder | Sep 20, 2018 | Risk Management
“What do you think the difference is between GRC and IRM?” That’s a question we seem to hear over and over, and with good reason. I just heard that question again this week, and if you ask the internet, the answer you’ll get is underwhelming...
by Holly Giammanco | Sep 6, 2018 | Risk Management
There is a great article in the September 2018 issue of WIRED magazine titled The Code That Crashed The World. Authored by senior writer Andy Greenberg, it is “the untold story of the most devastating cyberattack in history”. The article is an in-depth...

by David Ponder | Jul 25, 2018 | Risk Management
I recently came across a YouTube video post on risk management that piqued my interest. I don’t usually scour social media for risk management posts, but this one claimed to be a controversial stance, as emphasized Risk Management 1 and Risk Management 2 as...

by Holly Giammanco | Jul 10, 2018 | Risk Management
Control self-assessments, or CSAs, are where the leaders and supporting teams of business units, departments, or business processes directly engage in an evaluation of the objectives, risks, controls and processes they are responsible for managing. An effective CSA...
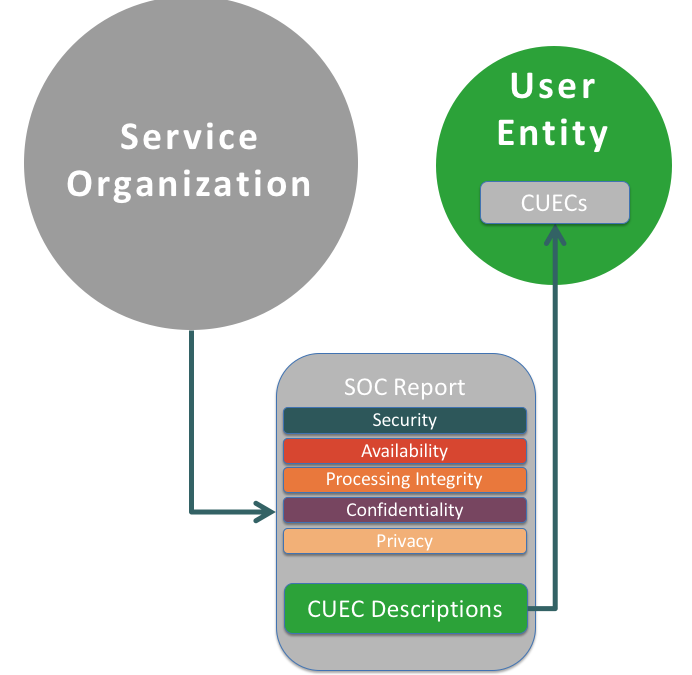
by David Ponder | Jun 27, 2018 | Risk Management, SOC Reports
“Dear vendor, your Service Provider’s SOC report doesn’t cover the services you’re providing us. Thank you for providing Amazon’s/Google’s/Microsoft’s SOC 2 report, but can you please provide a SOC 2 report that covers your...






